
Prepare for the SC-40 exam, work more productively not harder. Yes, contemporary society all pursues high efficiency, this is the requirement of the times, today we have prepared the latest SC-400 dumps with amazing efficiency to help you pass the Microsoft Information Protection Administrator exam.
Pass4itSure SC-400 dumps released https://www.pass4itsure.com/sc-400.html In 2023, with 154 new questions, it integrates the latest exam practice questions to help you pass worry-free, all you need to do is do the questions with peace of mind.
What are Pass4itSure SC-400 dumps?
In short, it is a compilation of the latest Microsoft SC-400 exam learning materials, providing you with the latest exam practice questions, all centered around the real exam content. SC-400 dumps, a collection of questions distilled from painstaking work, expert preparation, and constant feedback, will easily pass the SC-400 exam by practicing it.
Difficulties you will encounter in preparing for the SC-400 exam
- It takes a lot of time from the start of preparation to taking the exam. For example, study time cannot be centrally arranged. It may not take as much time to study for the SC-400 exam all day, but it is always busy.
- There is no purpose to prepare for the exam, it is pointless to work hard here today and prepare here tomorrow. Be smarter in preparation, not without planning.
To sum up, there is no efficient way to prepare! Don’t worry, the Pass4itSure SC-400 dumps will help you, work more productively instead of harder.
You can learn SC-400 dumps free resources:
If you are looking for the latest SC-400 pdf: https://drive.google.com/file/d/1k7T6S818xcR8k_UAlN85UpSKervW6QLB/view?usp=share_link
Microsoft Role-based SC-400 dumps online exam questions free
Question 1:
You have a Microsoft 365 tenant that uses Microsoft Office 365 Message Encryption (OME).
You need to ensure that any emails containing attachments sent to [email protected] are encrypted automatically by using OME. What should you do?
A. From the Exchange admin center, create a new sharing policy.
B. From the Microsoft 365 security center, create a Safe Attachments policy.
C. From the Exchange admin center, create a mail flow rule.
D. From the Microsoft 365 compliance center, configure an auto-apply retention label policy.
Correct Answer: C
You can create mail flow rules to help protect the email messages you send and receive. You can set up rules to encrypt any outgoing email messages and remove encryption from encrypted messages coming from inside your organization or from replies to encrypted messages sent from your organization.
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/define-mail-flow-rules-to-encrypt-email?view=o365-worldwide
Question 2:
You plan to implement sensitivity labels for Microsoft Teams.
You need to ensure that you can view and apply sensitivity labels to new Microsoft Teams sites.
What should you do first?
A. Run the Set-apposite cmdlet.
B. Configure the EnableMTPLabels Azure Active Directory (Azure AD) setting.
C. Create a new sensitivity label scoped to Groups and sites.
D. Run the Execute-AzureAdLabelSync cmdlet.
Correct Answer: C
Question 3:
You have a new Microsoft 365 tenant.
You need to ensure that custom trainable classifiers can be created in the tenant.
To which role should you be assigned to perform the configuration?
A. Security Administrator
B. Security operator
C. Global administrator
D. Compliance administrator
Correct Answer: D
Question 4:
You have a Microsoft 365 tenant that uses 100 data loss prevention (DLP) policies. A Microsoft Exchange administrator frequently investigates emails that were blocked due to DLP policy violations.
You need to recommend which DLP report the Exchange administrator can use to identify how many messages were blocked based on each DLP policy. Which report should you recommend?
A. Third-party DLP policy matches
B. DLP policy matches
C. DLP incidents
D. False positive and override
Correct Answer: B
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-learn-about-dlp?view=o365-worldwide
Question 5:
HOTSPOT
You have a Microsoft 365 tenant that uses a domain named contoso.com.
A user named User1 leaves your company. The mailbox of User1 is placed on Litigation Hold, and then the account of User1 is deleted from Azure Active Directory (Azure AD).
You need to copy the content of the User1 mailbox to a folder in the existing mailbox of another user named User2. How should you complete the PowerShell command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
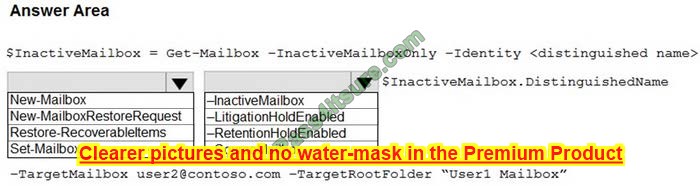
Correct Answer:
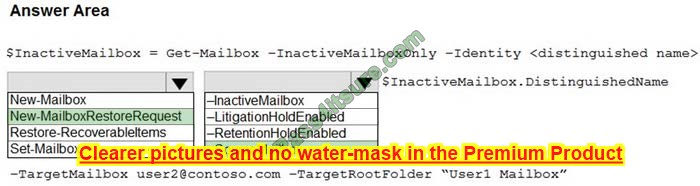
References: https://docs.microsoft.com/en-us/microsoft-365/compliance/restore-an-inactive-mailbox?view=o365-worldwide
Question 6:
HOTSPOT
You plan to create a custom trainable classifier based on an organizational form template.
You need to identify which role-based access control (RBAC ) role is required to create the trainable classifier and where to the classifier. The solution must use the principle of least privilege.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
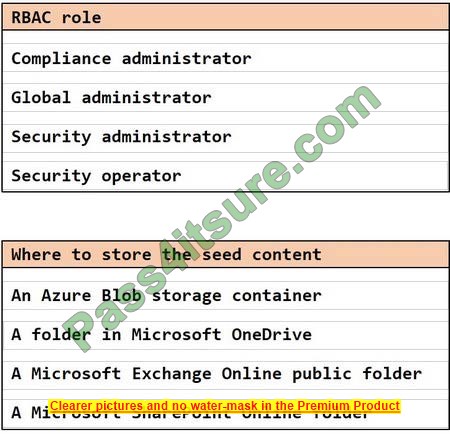
Correct Answer:
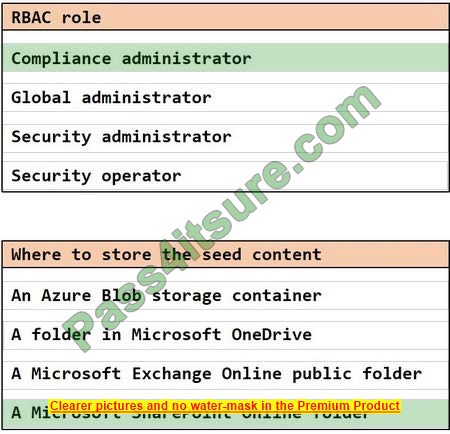
Question 7:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear on the review screen.
You are configuring a file policy in Microsoft Cloud App Security.
You need to configure the policy to apply to all files. Alerts must be sent to every file owner who is affected by the policy. The policy must scan for credit card numbers, and alerts must be sent to the Microsoft Teams site of the affected
department.
Solution: You use the Built-in DLP inspection method and send alerts by email.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
Alerts must be sent to the Microsoft Teams site of the affected department. A Microsoft Power Automate playbook should be used.
Reference: https://docs.microsoft.com/en-us/cloud-app-security/content-inspection-built-in https://docs.microsoft.com/en-us/cloud-app-security/flow-integration
Question 8:
HOTSPOT
You have a Microsoft 365 E5 tenant that contains three groups named Group1, Group2, and Group3.
You have the users shown in the following table.
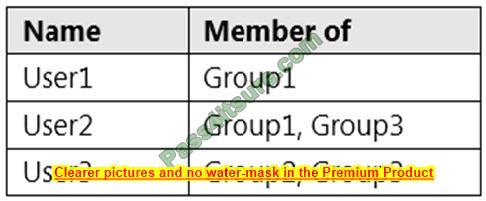
You have the sensitivity labels shown in the following exhibit.
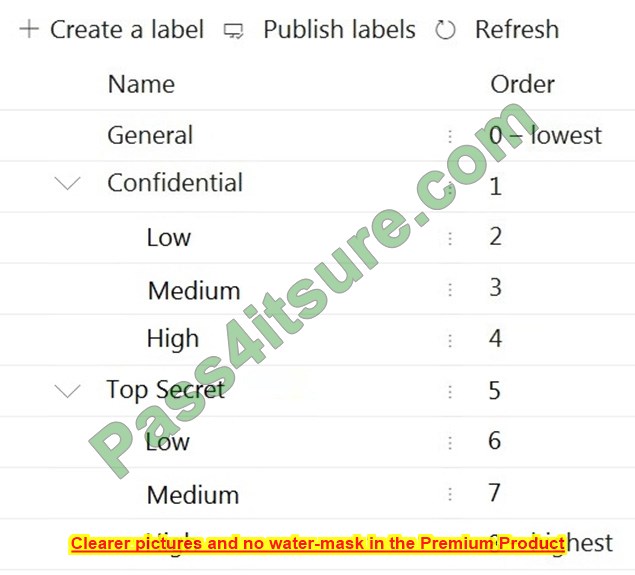
You have the label policies shown in the following table.
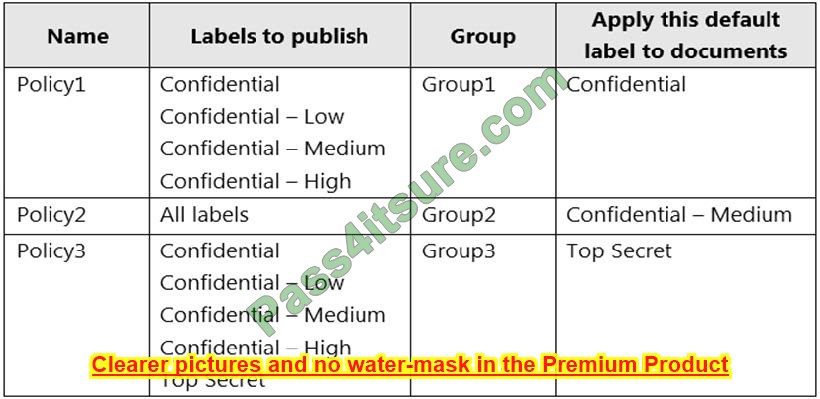
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
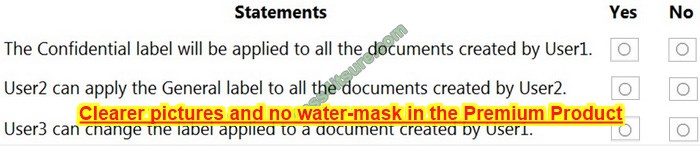
Correct Answer:
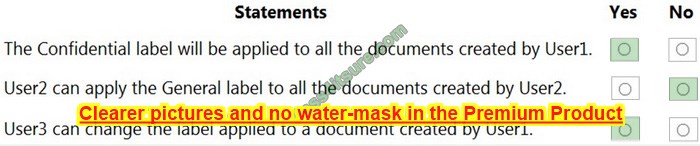
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide
Question 9:
You have a Microsoft 365 E5 tenant that contains a user named User1.
You need to identify the type and number of holds placed on the mailbox of User1.
What should you do first?
A. From the Microsoft 365 compliance center, create an eDiscovery case.
B. From Exchange Online PowerShell, run the Get-Mailbox cmdlet.
C. From the Microsoft 365 compliance center, run a content search.
D. From Exchange Online PowerShell, run the Get-HoldCompliancePolicy cmdlet.
Correct Answer: B
Question 10:
You have a Microsoft 365 E5 tenant.
You need to add a new keyword dictionary.
What should you create?
A. a trainable classifier
B. a sensitivity label E3
C. a sensitive info type
D. a retention policy
Correct Answer: C
Question 11:
You are evaluating the technical requirements for the DLP reports. Which user can currently view the DLP reports?
A. Admin4
B. Admin1
C. Admin5
D. Admin2
E. Admin3
Correct Answer: E
Question 12:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear on the review screen.
You have a Microsoft 365 tenant and 500 computers that run Windows 10. The computers are onboarded to the Microsoft 365 compliance center.
You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents.
Solution: From the Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings, you add the application to the unallowed apps list.
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
Unallowed apps are a list of applications that you create which will not be allowed to access a DLP-protected file.
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-using?view=o365-worldwide
Question 13:
You have a Microsoft 365 tenant that uses the following sensitivity labels:
1. Confidential
2. Internal
3. External
The labels are published by using a label policy named Policy1. Users report that Microsoft Office for the web apps does not display the Sensitivity button. The Sensitivity button appears in Microsoft 365 Apps that are installed locally.
You need to ensure that the users can apply sensitivity labels to content when they use Office for web apps. Solution: You run the Execute-AzureAdLabelSync cmdlet. Does this meet the goal?
A. Yes
B. No
Correct Answer: A
Question 14:
You have a Microsoft 365 tenant. You have a Microsoft SharePoint Online site that contains employment contracts in a folder named EmploymentContracts. All the files in EmploymentContracts are marked as records.
You need to recommend a process to ensure that when a record is updated, the previous version of the record is kept as a version of the updated record. What should you recommend?
A. Upload an updated file plan that contains the record definition.
B. Unlock the record, modify the record, and then lock the record.
C. Create a copy of the record and enter a version in the file metadata.
D. Create a new label policy associated with an event that will apply to the record.
Correct Answer: B
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/record-versioning?view=o365-worldwide
Question 15:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear on the review screen. You have a Microsoft 365 tenant and 500 computers that run Windows 10. The computers are onboarded to the Microsoft 365 compliance center.
You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents.
Solution: From the Cloud App Security portal, you mark the application as Unsanctioned. Does this meet the goal?
A. Yes
B. No
Correct Answer: B
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-using?view=o365-worldwide
In a word:
Use the SC-400 dumps https://www.pass4itsure.com/sc-400.html (Pass4itSure has been updated) to practice the exam questions wholeheartedly, and as always, like we like to say, work efficiently instead of trying harder! Successful exam success must be yours!