This is the latest Microsoft AZ-500 dumps exam material, providing 486 latest exam questions and answers, worthy of candidates AZ-500 Exam “Microsoft Azure Security Technologies” to follow!
You can use Microsoft AZ-500 dumps: https://www.pass4itsure.com/az-500.html to prepare ahead of time for the AZ-500 exam! And you can choose PDF or VCE practice tools to help you practice easily,
You are guaranteed to enjoy this exercise program with ease! And 100% pass the exam.
Learn more about the Microsoft AZ-500 exam
Skills measured:
- Manage identity and access (25–30%)
- Secure networking (20–25%)
- Secure computing, storage, and databases (20–25%)
- Manage security operations (25–30%)
| Exam name: | Microsoft Azure Security Technologies |
| Exam code: | AZ-500 |
| Number of exam questions: | 40-60 (*the number can vary depending on the exam) |
| Length of Test: | 150-210 minutes |
| Passing Score: | 70% – 700 points (out of 1000 points) |
| Price: | $165 USD* |
| Languages: | English, Japanese, Chinese (Simplified), Korean, German, French, Spanish, Portuguese (Brazil), Arabic (Saudi Arabia), Russian, Chinese (Traditional), Italian, Indonesian (Indonesia) |
| Retirement date: | None |
| Testing Provider: | Pearson VUE |
| More certification preparation details: | Learn Microsoft |
Practice online Microsoft AZ-500 dumps exam material
| From | Number of exam questions | Relevant certification |
| Pass4itsure | 15/486 | Microsoft Azure |
Question 1:
You have been tasked with configuring an access review, which you plan to assign to a new collection of reviews. You also have to make sure that the reviews can be reviewed by resource owners.
You start by creating an access review program and an access review control.
You now need to configure the Reviewers.
Which of the following should you set Reviewers to?
A. Selected users.
B. Members (Self).
C. Group Owners.
D. Anyone.
Correct Answer: C
In the Reviewers section, select either one or more people to review all the users in scope. Or you can select to have the members review their own access. If the resource is a group, you can ask the group owners to review it.

Reference: https://docs.microsoft.com/en-us/azure/active-directory/governance/create-access-review https://docs.microsoft.com/en-us/azure/active-directory/governance/manage-programs-controls
Question 2:
You have an Azure subscription that contains the Azure Log Analytics workspaces shown in the following table.

You create the virtual machines shown in the following table.
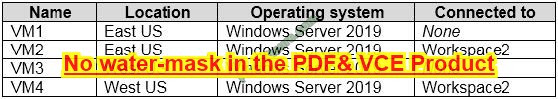
You plan to use Azure Sentinel to monitor Windows Defender Firewall on the virtual machines. Which virtual machines you can connect to Azure Sentinel?
A. VM1 and VM3 only
B. VM1 Only
C. VM1 and VM2 only
D. VM1, VM2, VM3 and VM4
Correct Answer: D
Reference: https://docs.microsoft.com/en-us/azure/sentinel/connect-windows-firewall
Question 3:
You have an Azure SQL database.
You implement Always Encrypted.
You need to ensure that application developers can retrieve and decrypt data in the database.
Which two pieces of information should you provide to the developers? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. a stored access policy
B. a shared access signature (SAS)
C. The column encryption key
D. user credentials
E. the column master key
Correct Answer: CE
Always Encrypted uses two types of keys: column encryption keys and column master keys. A column encryption key is used to encrypt data in an encrypted column. A column master key is a key-protecting key that encrypts one or more column encryption keys.
Question 4:
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
You need to configure diagnostic settings for contoso.com. The solution must meet the following requirements:
1.
Retain logs for two years.
2.
Query logs by using the Kusto query language.
3.
Minimize administrative effort. Where should you store the logs?
A. an Azure event hub
B. an Azure Log Analytics workspace
C. An Azure Storage account
Correct Answer: B
https://docs.microsoft.com/en-us/azure/azure-monitor/log-query/get-started-queries
Question 5:
SIMULATION
You need to email an alert to a user named [email protected] if the average CPU usage of a virtual machine named VM1 is greater than 70 percent for a period of 15 minutes.
To complete this task, sign in to the Azure portal.
A. See the explanation below.
Correct Answer: A
Create an alert rule on a metric with the Azure portal
1.
In the portal, locate the resource, here VM1, you are interested in monitoring and select it.
2.
Select Alerts (Classic) under the MONITORING section. The text and icon may vary slightly for different resources.
3.
Select the Add metric alert (classic) button fill in the fields as per below, and click OK.
Metric: CPU Percentage Condition: Greater than Period: Over last 15 minutes Notify via email Additional administrator email(s): [email protected]

Reference: https://docs.microsoft.com/en-us/azure/sql-database/sql-database-insights-alerts-portal
Question 6:
You have an Azure subscription that contains the resources shown in the following table.

1
You need to ensure that ServerAdmins can perform the following tasks:
1.
Create virtual machine to the existing virtual network in RG2 only.
2.
The solution must use the principle of least privilege.
Which two role-based access control (RBAC) roles should you assign to ServerAdmins?
Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. the Contributor role for the subscription
B. the Network Contributor role for RG2
C. A custom RBAC role for the subscription
D. a custom RBAC role for RG2
E. the Network Contributor role for RG1.
F. the Virtual Machine Contributor role for RG1.
Correct Answer: DF
Reference: https://docs.microsoft.com/en-us/azure/role-based-access-control/built-in-roles
Question 7:
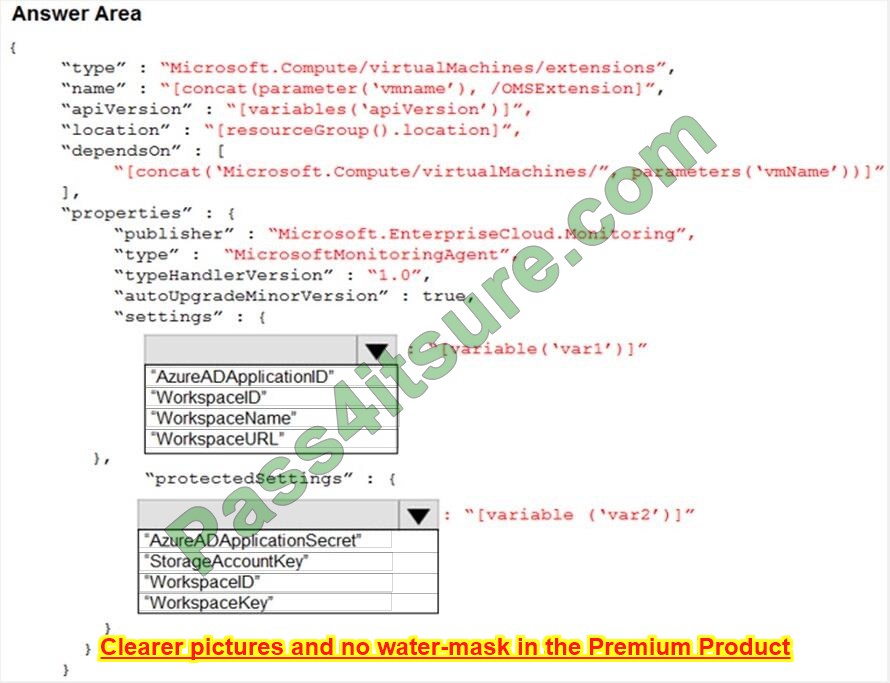
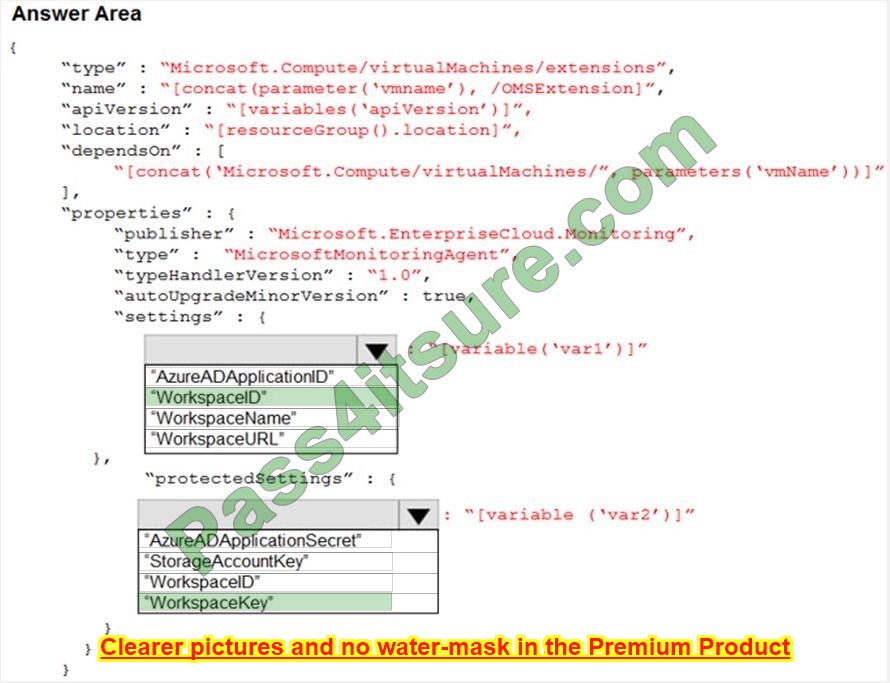
You plan to use Azure Monitor Logs to collect logs from 200 servers that run Windows Server 2016.
You need to automate the deployment of the Log Analytics Agent to all the servers by using an Azure Resource Manager template.
How should you complete the template? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
Question 8:
Your company has an Azure Active Directory (Azure AD) tenant named contoso.com.
The company is developing an application named App1. App1 will run as a service on the server that runs Windows Server 2016. App1 will authenticate to contoso.com and access Microsoft Graph to read directory data.
You need to delegate the minimum required permissions to App1.
Which three actions should you perform in sequence from the Azure portal? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
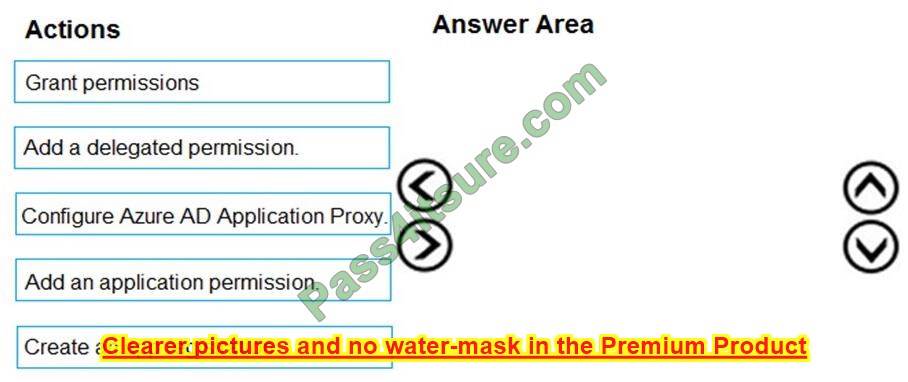
Correct Answer:
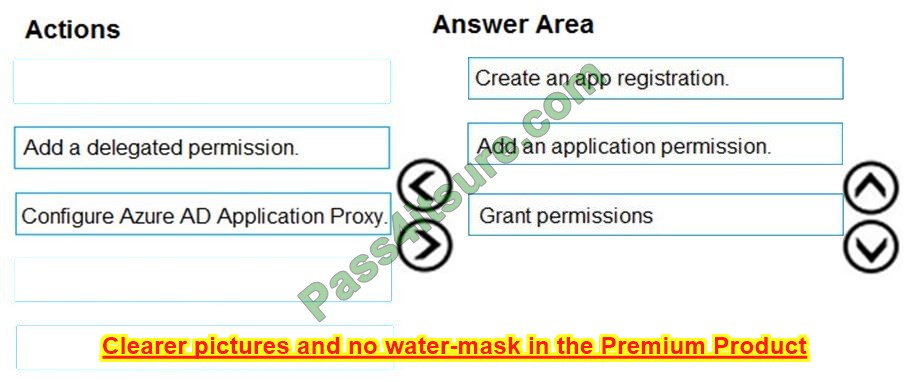
Step 1: Create an app registration
First, the application must be created/registered.
Step 2: Add an application permission
Application permissions are used by apps that run without a signed-in user present.
Step 3: Grant permissions
Incorrect Answers:
Delegated permission
Delegated permissions are used by apps that have a signed-in user present.
Application Proxy:
Azure Active Directory\’s Application Proxy provides secure remote access to on-premises web applications.
References:
https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-permissions-and-consent
Question 9:
HOTSPOT
You have an Azure Storage account that contains a blob container named container1 and a client application named App1.
You need to enable App1 access to container1 by using Azure Active Directory (Azure AD) authentication.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
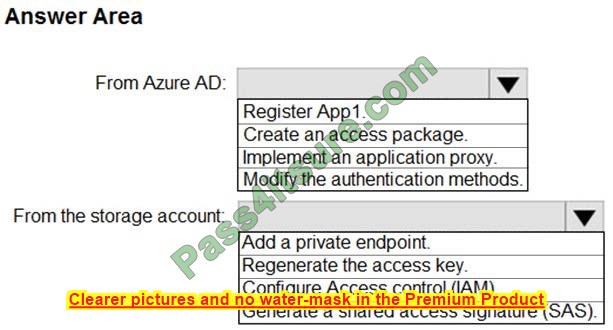
Correct Answer:
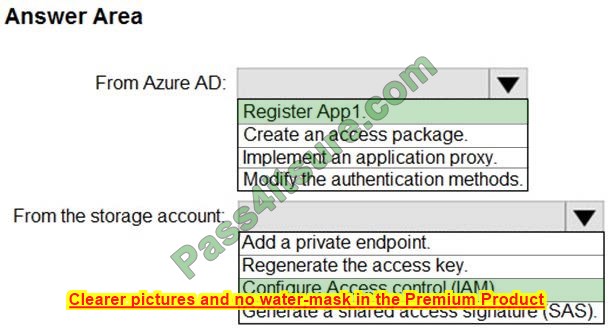
Reference:
https://azure.microsoft.com/en-in/blog/announcing-the-preview-of-aad-authentication-for-storage/
Question 10:
You have an Azure subscription that contains a user named UseR1.
You need to ensure that UseR1 can perform the following tasks:
1.
Create groups.
2.
Create access reviews for role-assignable groups.
3.
Assign Azure AD roles to groups.
The solution must use the principle of least privilege.
Which role should you assign to User1?
A. Groups administrator
B. Authentication administrator
C. Identity Governance Administrator
D. Privileged role administrator
Correct Answer: D
Privileged Role Administrator Users with this role can manage role assignments in Azure Active Directory, as well as within Azure AD Privileged Identity Management. They can create and manage groups that can be assigned to Azure AD roles. In addition, this role allows management of all aspects of Privileged Identity Management and administrative units.
Incorrect:
* Identity Governance Administrator Users with this role can manage Azure AD identity governance configuration, including access packages, access reviews, catalogs, and policies, ensuring access is approved and reviewed and guest users who no longer need access are removed.
Reference: https://learn.microsoft.com/en-us/azure/active-directory/roles/permissions-referenc
Question 11:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription named Sub1.
You have an Azure Storage account named Sa1 in a resource group named RG1.
Users and applications access the blob service and the file service in Sa1 by using several shared access signatures (SASs) and stored access policies.
You discover that unauthorized users accessed both the file service and the blob service.
You need to revoke all access to Sa1.
Solution: You create a lock on Sa1.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
To revoke a stored access policy, you can either delete it or rename it by changing the signed identifier. Changing the signed identifier breaks the associations between any existing signatures and the stored access policy. Deleting or renaming the stored access policy immediately affects all of the shared access signatures associated with it.
References: https://docs.microsoft.com/en-us/rest/api/storageservices/Establishing-a-Stored-Access-Policy
Question 12:
You have an Azure subscription that contains a
You need to grant user1 access to blob1. The solution must ensure that the access expires after six days.
What should you use?
A. a shared access policy
B. a shared access signature (SAS)
C. Role-based access control (RBAC)
D. a managed identity
Correct Answer: C
Depending on how you want to authorize access to blob data in the Azure portal, you\’ll need specific permissions. In most cases, these permissions are provided via Azure role-based access control (Azure RBAC). For more information about Azure RBAC, see What is Azure role-based access control (Azure RBAC)?
https://learn.microsoft.com/en-us/azure/storage/blobs/authorize-data-operations-portal
Question 13:
You have an Azure subscription that contains an Azure key vault.
You need to configure the maximum number of days for which new keys are valid. The solution must minimize administrative effort.
What should you use?
A. Azure Purview
B. Key Vault properties
C. Azure Blueprints
D. Azure Policy
Correct Answer: D
Azure Policy example Usage Scenarios include:
You want to improve the security posture of your company by implementing requirements around minimum key sizes and maximum validity periods of certificates in your company\’s key vaults but you don’t know which teams will be compliant and which are not.
Note: Azure Policy is a governance tool that gives users the ability to audit and manage their Azure environment at scale. Azure Policy provides the ability to place guardrails on Azure resources to ensure they are compliant with assigned policy rules.
It allows users to perform audit, real-time enforcement, and remediation of their Azure environment. The results of audits performed by the policy will be available to users in a compliance dashboard where they will be able to see a drill down of which resources and components are compliant and which are not.
Reference: https://docs.microsoft.com/en-us/azure/key-vault/general/azure-policy
Question 14:
HOTSPOT
You have an Azure subscription that contains the resources shown in the following table.
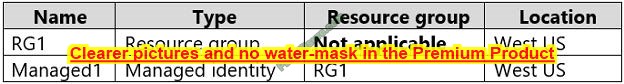
The subscription is linked to an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.

You create the groups shown in the following table.

The membership rules for Group 1 and Group 2 are configured as shown in the following exhibit.
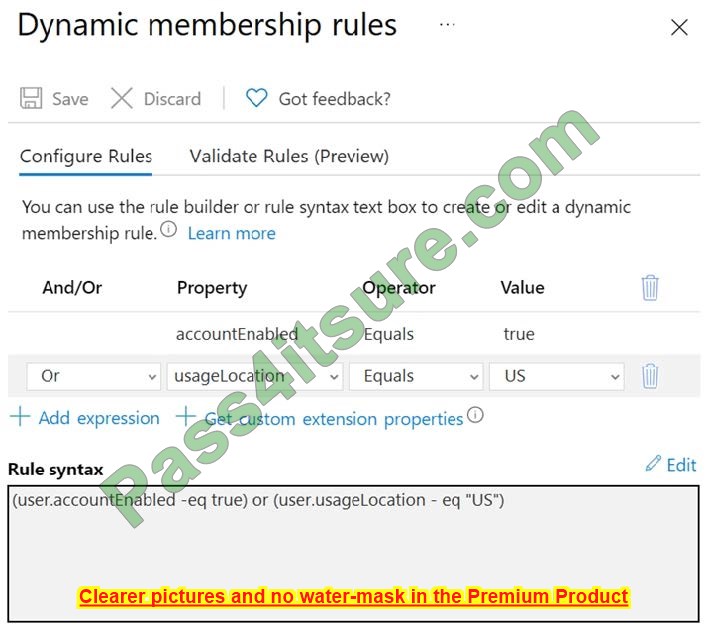
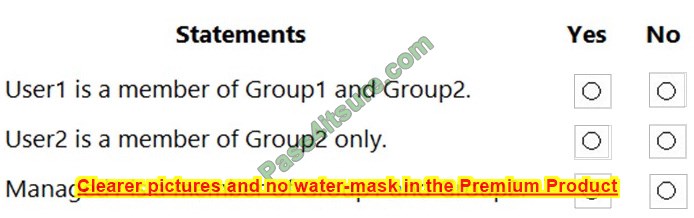
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
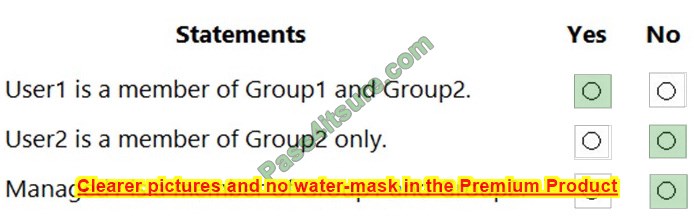
Reference: https://docs.microsoft.com/en-us/azure/active-directory/enterprise-users/groups-dynamic-membership
Question 15:
Note: The question is included in a number of questions that depict the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your company has an Active Directory forest with a single domain, named weylandindustries.com. They also have an Azure Active Directory (Azure AD) tenant with the same name.
You have been tasked with integrating Active Directory and the Azure AD tenant. You intend to deploy Azure AD Connect.
Your strategy for the integration must make sure that password policies and user logon limitations affect user accounts that are synced to the Azure AD tenant, and that the amount of necessary servers is reduced.
Solution: You recommend the use of password hash synchronization and seamless SSO.
Does the solution meet the goal?
A. Yes
B. No
Correct Answer: A
Password hash synchronization requires the least effort regarding deployment, maintenance, and infrastructure. This level of effort typically applies to organizations that only need their users to sign in to Office 365, SaaS apps, and other Azure AD-based resources. When turned on, password hash synchronization is part of the Azure AD Connect sync process and runs every two minutes.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-pta
…
Microsoft AZ-500 dumps are the latest exam material, edited, reviewed, corrected, and participated in the actual verification by the Pass4itsure Microsoft professional team to ensure authenticity and effectiveness!
This is the best Microsoft AZ-500 dumps exam material, You only need to spend 2-3 days of serious practice, and you can ensure that you pass the AZ-500 Exam “Microsoft Azure Security Technologies” easily.