Cabinetdetherapies collects 50 authentic Cisco CCDP 300-320 Exam questions and Answers,and 300-320 pdf online sharing downloads, we help you improve your skills if you want to pass Cisco 300-320 Exams need to be noted: (Duration 75 minutes (60 – 70 questions)),(available Languages English), Exam Policies. It is strongly recommended, but not required, that students have the following knowledge and skills:
- Internetworking technologies, Cisco products, and Cisco IOS features
- Cisco Certified Network Associate (CCNA) level-of-knowledge
- Designing for Cisco Internetwork Solutions (DESGN) level-of-knowledge
- Implementing Cisco IP Switched Networks (SWITCH) level-of-knowledge
- Implementing Cisco IP Routing (ROUTE) level-of-knowledge
if you want to get “Designin Cisco Network Service Architectures (ARCH) v3.0” is the 300-320 exam dump, CISCO 300-320 exam certification.
Cabinetdetherapies recommends that you: https://www.pass4itsure.com/300-320.html (Q&As: 600 PDF + VCE) is frequently updated and reviewed to pass the exam quickly.
[PDF]Free Cisco CCDP 300-320 dumps download from Google Drive: https://drive.google.com/open?id=1gcv6doYWV3faGu3L-PtZ4YfpOCMmcn0O
[PDF]Free Full Cisco dumps download from Google Drive: https://drive.google.com/open?id=1Qzc3W-UXHXeCJZQZIsYAVUuIacAB5JWN
300-320 – Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/arch-300-320.html
Free 50 Cisco CCDP 300-320 Practice test questions and answers
QUESTION 1
In which OSI layer does IS-IS operate?
A. Layer 1
B. Layer 2
C. Layer 3
D. Layer 4
Correct Answer: B
QUESTION 2
Which two types of authentication mechanisms can be used by VRRP for security? (Choose two.)
A. SHA-1
B. MD5
C. SHA-256
D. plaintext authentication
E. PEAP
Correct Answer: BD
QUESTION 3
NAC: Simple access control at user and device contextual level. Which features are needed ? (Choose Two)
A. secure access control
B. TrustSec
C. ISE
D. NAC agent
Correct Answer: CD
QUESTION 4
Which OSPF concept is used to relate areas to the backbone area through another area?
A. Virtual Links
B. Backup Links
C. Inter-backbone Links
D. Point-to-point Links
Correct Answer: A
QUESTION 5
What protocol is used for connectivity between VSS layers?
A. PAgP
B. IVR
C. ISL
D. VSL
Correct Answer: D
QUESTION 6
Which technology should a network designer combine with VSS to ensure a loop free topology with optimal convergence time?
A. Portfast
B. UplinkFast
C. RPVST +
D. Multichassis EtherChannel
Correct Answer: D
QUESTION 7
ACME corporation owns a single MDS. Which two SAN tools can be used to optimize the use and cost of the switching hardware? (Choose two.)
A. zoning
B. IVR
C. VSAN
D. iSCSI
Correct Answer: BC
QUESTION 8
If your enterprise is connected to 2 ISP, which method could you use to prevent being used as a transit network? (Choose Two)
A. filter outbound
B. filter inbound
C. throw both ISP
D. choose only one ISP
E. Allow every routes inbound
Correct Answer: AE
QUESTION 9
Which two options improve BGP scalability in a large autonomous system? (Choose two.)
A. route reflectors
B. route redistribution
C. confederations
D. communities
Correct Answer: AC
QUESTION 10
What is one limitation of MPLS Layer 3 VPN networks?
A. They require less powerful routers with limited capabilities
B. They require the customer to control routing
C. They support only IP traffic
D. PE routers are underutilized
Correct Answer: C
QUESTION 11
Which ASA to action with Web traffic to treat both HTTP and HTTPS for local internet proxy?
A. Redirect traffic HTTP & HTTPS to WSA using wccp
B. Send traffic for inspection to CWS
C. Send traffic to a different port for http & https monitoring to WSA using L2TP.
D. Use IPS module in ASA for inspection
Correct Answer: A
QUESTION 12
An engineer is designing a new data center network so that the topology maintains fewer uplinks to the aggregation layer to reduce STP processing requirements.
What data center topology meets the RFP requirements?
A. mesh
B. top of rack
C. star
D. end of row
Correct Answer: D
QUESTION 13
On which two types of links should routing protocol peerings be established according to best practice? (Choose two.)
A. distribution links
B. end user links
C. transit links
D. core links
Correct Answer: CD
QUESTION 14
Company has asked for an OOB management network design. Which option is one Cisco best practice parameter that must be followed?
A. Data networks must be limited to SSH, NTP, FTP, SNMP and TaCACS+ protocols
B. Data networks must never traverse the management network
C. Data networks and management networks must be in the routing table
D. Data networks must traverse the management network as a backup path
Correct Answer: B
QUESTION 15
A company have single ASA hardware box and they need to separate company departments in way that they can apply different rules on them, ACL, NAT, and so
on…
Which mode is needed?
A. routed mode
B. transparent mode
C. multiple context mode
D. active failover mode
Correct Answer: C
QUESTION 16
When designing data centers for multitenancy, which two benefits are provided by the implementation of VSAN and zoning? (Choose two)
A. VSAN provides a means of restricting visibility and connectivity among devices connected to a zone
B. VSANs have their own set of services and address space, which prevents an issue in one VSAN from affecting others
C. Zones provide the ability to create many logical SAN fabrics on a single Cisco MDS 9100 family switch
D. VSANs and zones use separate fabrics
E. Zones allow an administrator to control which initiators can see which targets
Correct Answer: BE
QUESTION 17
Which two methods are available to connect a Cisco IOS device to an active directory domain for authentication? (Choose two)A. LDAP (Lightweight Directory Access Protocol)
B. Radius
C. TACACS+
D. AAA
Correct Answer: AB
QUESTION 18
To which network layer should Cisco Express Forwarding be tuned to support load balancing and to make more informed forwarding decisions?
A. Layer 1
B. Layer 2
C. Layer 3
D. Layer 4
E. Layer 5
F. Layer 6
G. Layer 7
Correct Answer: D
QUESTION 19
An engineer is designing a Multichassis Etherchannel using VSS. Which network topology is the result?
A. Looped
B. Ring
C. Hybrid
D. Star
Correct Answer: D
QUESTION 20
A company wants to configure BGP on a router so that other BGP neighbors cannot influence the path of a particular route .which action must be taken to accomplish this configuration ?
A. Configure a low router ID for the route
B. Configure a high local preference for the route
C. Configure a high weight for the route
D. Configure a low MED for the route
Correct Answer: B
QUESTION 21
A Layer 2 switch in the network has recently started broadcasting traffic out of every port and is impacting network performance. The engineering department
determines that a MAC overflow attack is the cause. Which two features can protect and mitigate the damage of the attacks? (Choose two.)
A. Storm Control
B. Port Security
C. SPAN
D. BPDU Filters
E. IP Source Guard
F. VACLs
Correct Answer: AB
QUESTION 22
Which two features can you implement to control which networks are advertised by a BGP router? (Choose two.)
A. prefix lists
B. route maps
C. policy maps
D. router SNMP statements
E. crypto maps
Correct Answer: AB
QUESTION 23
What location are security policies enforced in ACI?
A. leaf
B. spine
C. core
D. distribution
Correct Answer: A
QUESTION 24
One-to-one ratio mapping for access switches close to servers.
A. ToR
B. EoR
Correct Answer: A
QUESTION 25
How does stub routing affect transit routes in EIGRP?
A. Transit routes are passed from a stub network to a hub network.
B. It is designed to prevent the distribution of external routes.
C. It prevents the hub router from advertising networks learned from the spokes.
D. Transit routes are filtered from stub networks to the network hub.
Correct Answer: B
QUESTION 26
A customer would like to implement a firewall to secure an enterprise network. However, the customer is unable to allocate any new subnets. What type of firewall
mode must be implemented?
A. routed
B. active/standby
C. transparent
D. virtual
E. active/active
F. zone based
Correct Answer: C
QUESTION 27
A network engineer must use an Internet connection to provide backup connectivity between two sites. The backup connection must be encrypted and support
multicast.
Which technology must be used?
A. GRE over IPsec
B. GETVPN
C. IPsec direct encapsulation
D. DMVPN
Correct Answer: A
QUESTION 28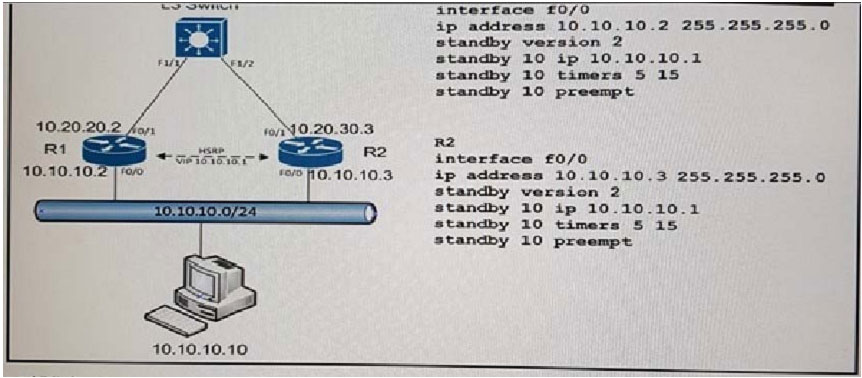 Refer to the exhibit. A customer wants to use HSRP as a First Hop Redundancy Protocol. Both routers are currently running and all interfaces are active. Which
Refer to the exhibit. A customer wants to use HSRP as a First Hop Redundancy Protocol. Both routers are currently running and all interfaces are active. Which
factor determines which router becomes the active HSRP device?
A. the router with the highest MAC address for the respective group
B. the router with the highest IP address for the respective group
C. the router that boots up last
D. the router with the highest interface bandwidth for the respective group
Correct Answer: B
QUESTION 29
At which layer in the ACI fabric are policies enforced?
A. leaf
B. spine
C. APIC
D. endpoint
Correct Answer: C
QUESTION 30
An OSPF router should have a maximum of how many adjacent neighbors?
A. 100
B. 80
C. 60
D. 50Correct Answer: C
QUESTION 31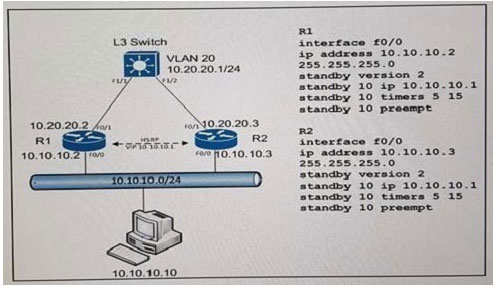
Refer to the exhibit. A customer discovers router R1 remains active even when R1 uplink (F0/1) is down. Which two commands can be applied to R1 to allow R2
to take over as the HSRP active? (Choose two.)
A. Standby 10 track 50
B. Standby 10 track 50 decrement 20
C. Track 50 ip route 10.10.10.0/24 reachability
D. Standby 10 track 50 shutdown
E. Track 50 interface Fa0/1 ip routing
Correct Answer: BE
QUESTION 32
The network engineering team for a large university must increase the security within the core of the network by ensuring that IP traffic only originates from a
network segment that is assigned to that interface in the routing table. Which technology must be chosen to accomplish this requirement?
A. VLAN access control lists
B. Unicast Reverse Path Forwarding
C. Intrusion prevention system
D. ARP inspection
Correct Answer: A
QUESTION 33
An engineer is working for a large scale cable TV provider that requires multicast on multisourced streaming video, but must not use any rendezvous point
mechanism. Which multicast protocol must be configured?
A. SSM
B. ASM
C. PIM-SM
D. BIDIR-PIM
Correct Answer: A
QUESTION 34
An engineer is considering uplink bandwidth over-subscription in a Layer 3 network design. Which option is the Cisco recommended over-subscription ratio for
uplinks between the distribution and core layers?
A. 3 to 1
B. 4 to 1
C. 6 to 1
D. 8 to 1
Correct Answer: B
QUESTION 35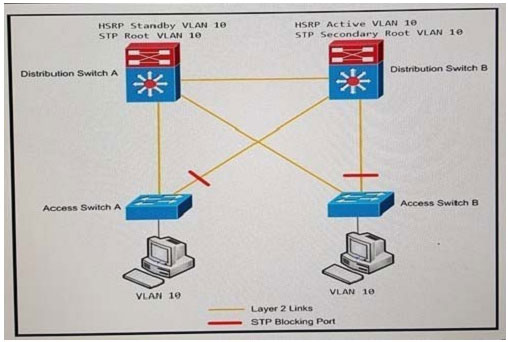
Refer to the exhibit. An engineer must provide a redesign for the distribution and access layers of the network. Which correction allows for a more efficient design?
A. Change the link between Distribution Switch A and Distribution Switch B to be a routed link.
B. Reconfigure the Distribution Switch A to become the HSRP Active.
C. Create an EtherChannel link between Distribution Switch A and Distribution Switch B.
D. Add a link between Access Switch A and Access Switch B.
Correct Answer: B
QUESTION 36
A network consultant is designing an Internet Edge solution and is providing the details around the flows supporting a local Internet Proxy. How is on-premises
web filtering supported?
A. A cisco ASA uses an IPS module to inspect HTTP and HTTPS traffic.
B. A Cisco ASA redirects HTTP and HTTPS traffic to the WSA using WCCP.
C. A Cisco ASA connects to the web security appliance via TLS to monitor HTTP and HTTPS traffic.
D. A Cisco ASA redirects HTTP and HTTPS traffic to CWS with a Web Security Connector.
Correct Answer: B
QUESTION 37
A network engineer must reduce the security risks on a BGP network. Which option helps to avoid rogue route injection, unwanted peering, and malicious BGP
activities?
A. Apply route maps and policies in route redistribution events.
B. Apply MD5 authentication between all BGP peers.
C. Encrypt all traffic with IPsec between neighbors.
D. Use GRE tunnels between all BGP peers.
Correct Answer: D
QUESTION 38
A network consultant is designing an enterprise network that includes an IPsec headend termination device. Which two capabilities are the most important to
consider when assessing the headend device’s scalability? (Choose two.)
A. bandwidth capabilities
B. packets per second processing capability
C. CPU capabilities
D. number of tunnels that can be aggregated
E. memory capabilities
Correct Answer: BD
QUESTION 39
When a site has Internet connectivity with two different ISP’s, which two strategies are recommended to avoid becoming a BGP transit site? (Choose two.)
A. accept all inbound routes from ISPs
B. advertise all routes to both ISPs.
C. filter routes inbound from the ISPs.
D. filter routes outbound to the ISPs.
E. use a single service provider.
Correct Answer: AD
QUESTION 40
An engineer is designing a Layer 3-enabled access layer. Which design recommendation must the engineer consider when deploying EIGRP routing within the
access layer?
A. Use the First Hop Redundancy Protocol on access layer switches.
B. Implement floating static routes on access switches for redundant links.
C. Enable multiple uplinks from each access switch stack to the distribution switches.
D. Configure all edge access layer switches to use a stub routing feature.
Correct Answer: D
QUESTION 41
The Cisco ACI fabric consists of which design at the physical layer?
A. three-tier core, aggregation, and access
B. collapsed core network
C. full mesh
D. spine-and-leaf
Correct Answer: D
QUESTION 42
What is the result of a successful RFP check?
A. The packet is dropped because it arrived on the interface used to route traffic back to the source address.
B. The packet is forwarded because it arrived on the interface used to route traffic back to the source address.
C. The packet is forwarded because it arrived on the interface used to route traffic to the destination address.
D. The packet is dropped because it arrived on the interface used to route traffic to the destination address.
Correct Answer: A
QUESTION 43
When you configure a multichassis setup with VSS, which link must be configured to extend the backplane between the two switches?
A. VSL
B. LCAP
C. PaGP
D. ISL
Correct Answer: D
QUESTION 44
An engineer is designing a network using RSTP. Several devices on the network support only legacy STP. Which outcome occurs?
A. RSTP and STP choose the protocol with the best performance.
B. RSTP and STP interoperate and fast convergence is achieved.
C. RSTP and STP are not compatible and legacy ports error disable.
D. RSTP and STP interoperate, but the fast convergence is not used.
Correct Answer: D
QUESTION 45
Which security function is inherent in an Application Centric Infrastructure network?
A. Intrusion Prevention
B. Intrusion Detection
C. Default Denial Network
D. Default Inter-EPG connectivity
Correct Answer: D
QUESTION 46
How does stub routing affect transit routes in EIGRP?
A. Transit routes are passed from a stub network to a hub network.
B. It is designed to prevent the distribution of external routes.
C. It prevents the hub router from advertising networks learned from the spokes.
D. Transit routes are filtered from stub networks to the network hub.
Correct Answer: B
QUESTION 47
A customer would like to implement a firewall to secure an enterprise network. However, the customer is unable to allocate any new subnets. What type of firewall
mode must be implemented?
A. routed
B. active/standby
C. transparent
D. virtual
E. active/active
F. zone based
Correct Answer: C
QUESTION 48
A network engineer must use an Internet connection to provide backup connectivity between two sites. The backup connection must be encrypted and support
multicast.
Which technology must be used?
A. GRE over IPsec
B. GETVPN
C. IPsec direct encapsulation
D. DMVPN
Correct Answer: A
QUESTION 49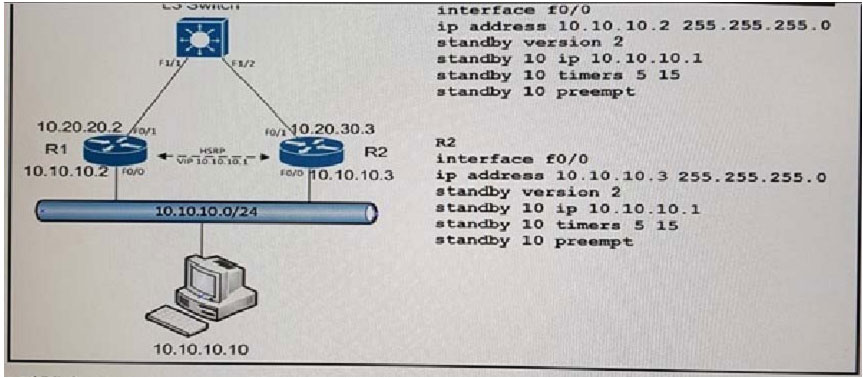 Refer to the exhibit. A customer wants to use HSRP as a First Hop Redundancy Protocol. Both routers are currently running and all interfaces are active. Which
Refer to the exhibit. A customer wants to use HSRP as a First Hop Redundancy Protocol. Both routers are currently running and all interfaces are active. Which
factor determines which router becomes the active HSRP device?
A. the router with the highest MAC address for the respective group
B. the router with the highest IP address for the respective group
C. the router that boots up last
D. the router with the highest interface bandwidth for the respective group
Correct Answer: B
QUESTION 50
At which layer in the ACI fabric are policies enforced?
A. leaf
B. spine
C. APIC
D. endpoint
Correct Answer: C
Conclusion:
Congratulations on reading here! Passing the Cisco CCDP 300-320 exam is not an easy task, you first need to understand the
details of the exam, and then you have to choose a truly valid 300-320 test material (Designin Cisco Network Service Architectures (ARCH) v3.0): https://www.pass4itsure.com/300-320.html (Q&As: 600 PDF + VCE),
finally you need to study hard and get ready for the exam.Choosing Pass4itsure will make your Cisco 300-320 exam very easy.
[PDF] Free Cisco CCDP 300-320 dumps download from Google Drive: https://drive.google.com/open?id=1gcv6doYWV3faGu3L-PtZ4YfpOCMmcn0O
[PDF] Free Full Cisco dumps download from Google Drive: https://drive.google.com/open?id=1Qzc3W-UXHXeCJZQZIsYAVUuIacAB5JWN
Pass4itsure Promo Code 15% Off